Table of Contents Show
In our previous blog post, we covered the basics of Google Cloud, including its pricing, security, and open-source adaptability. Now, join us as we take a closer look at how Google Cloud efficiently organizes resources within projects and ensures appropriate access to resources through Identity and Access Management (IAM).
We’ll also explore the different interaction techniques available, including web, command-line, and mobile apps. Don’t miss out on this opportunity to discover how to fully utilize the power of Google Cloud
Exploring the Google Cloud Resource Structure
Resource Structure
Picture a rapidly growing e-commerce company, “ShopTrendy,” which has recently adopted Google Cloud Platform (GCP) to manage its burgeoning IT infrastructure. As ShopTrendy’s online presence flourishes, grasping and managing the Google Cloud resource structure is essential for maintaining an organized and secure environment.
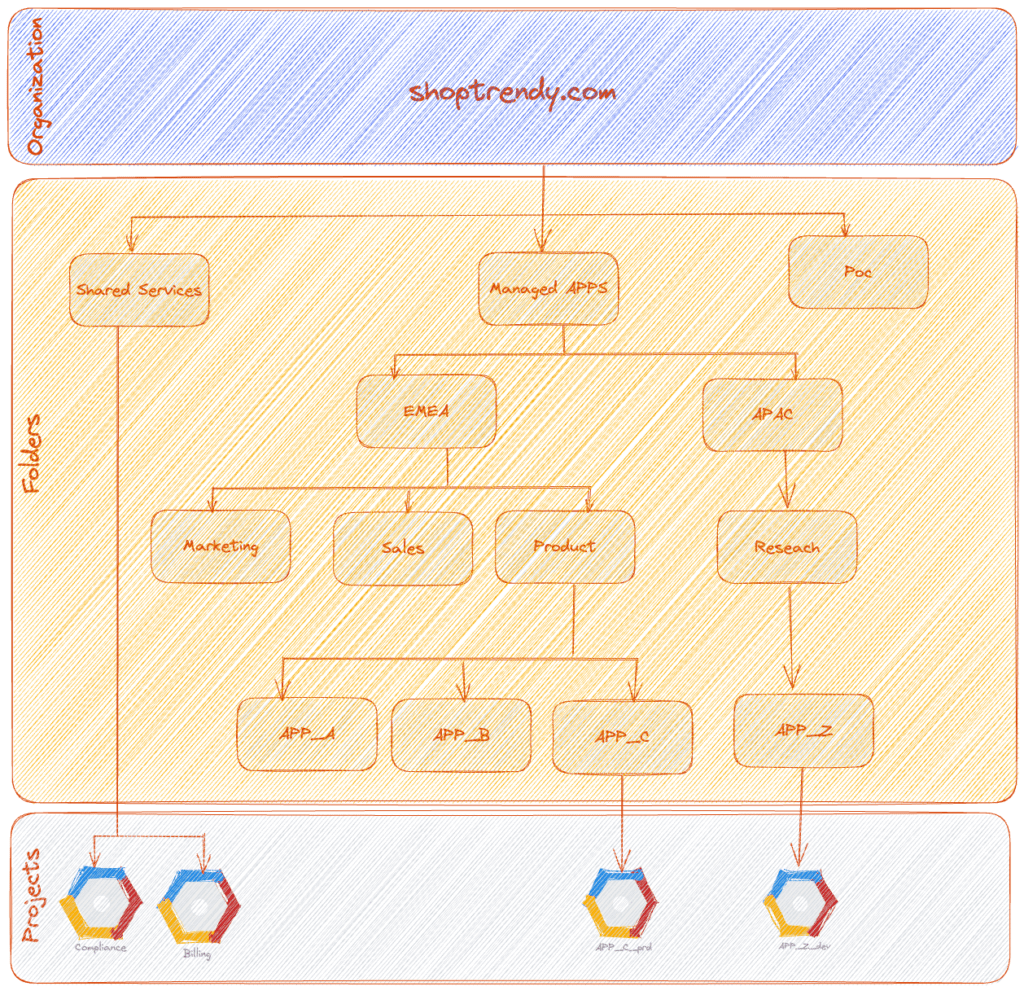
Google Cloud arranges resources using a hierarchy that allows enterprises like ShopTrendy to gain better control over their cloud assets. This hierarchy consists of the following four levels:
- Organization
The organization is the top level, representing ShopTrendy as a whole. It serves as a container for all the GCP resources owned by the company, enabling centralized management and the implementation of company-wide policies.

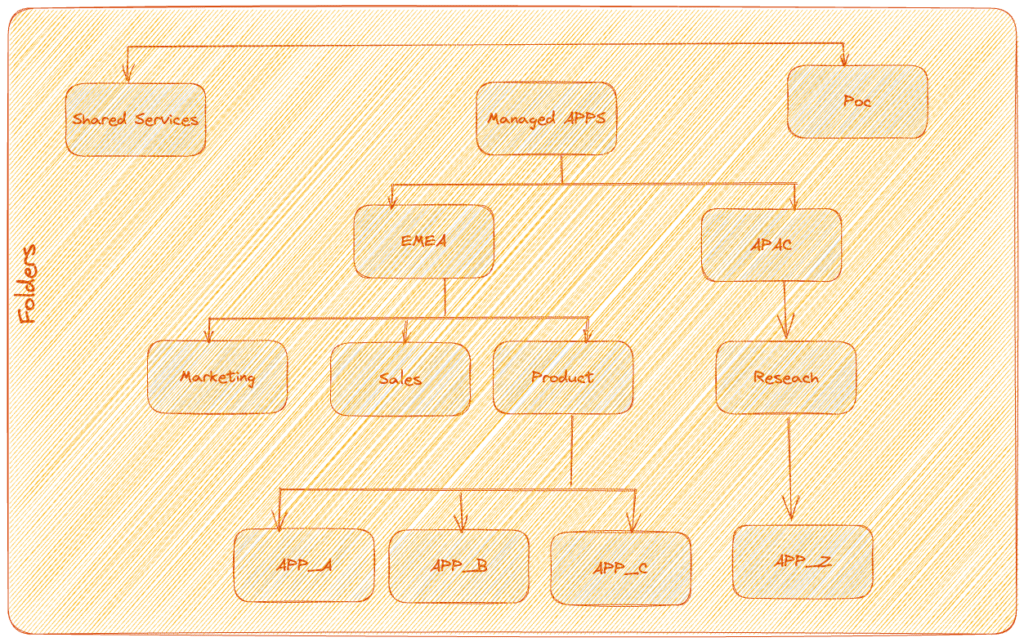
- Folders
Within the GCP hierarchy, folders are optional components that let ShopTrendy categorize projects according to their functions or departments. For instance, the company could establish separate folders for its business Regions (EMEA and APAC) and inside regions folders for marketing, sales, and product development teams, thereby maintaining organization and managing access effectively.
- Projects
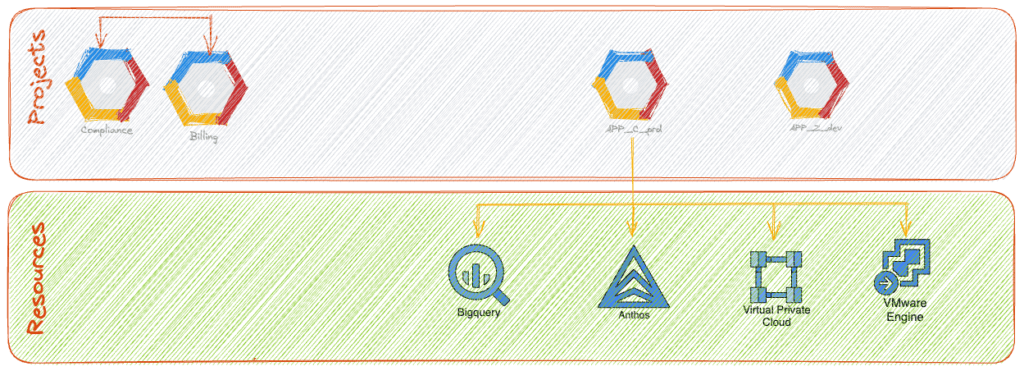
Projects are the core components of the GCP resource hierarchy. In the context of ShopTrendy, each project represents a specific application or service (APP_A ,APP_C ,etc,) . All GCP resources must belong to a project, ensuring resource isolation, access control, and billing management. Billing accounts linked to projects accurately track resource usage and costs.

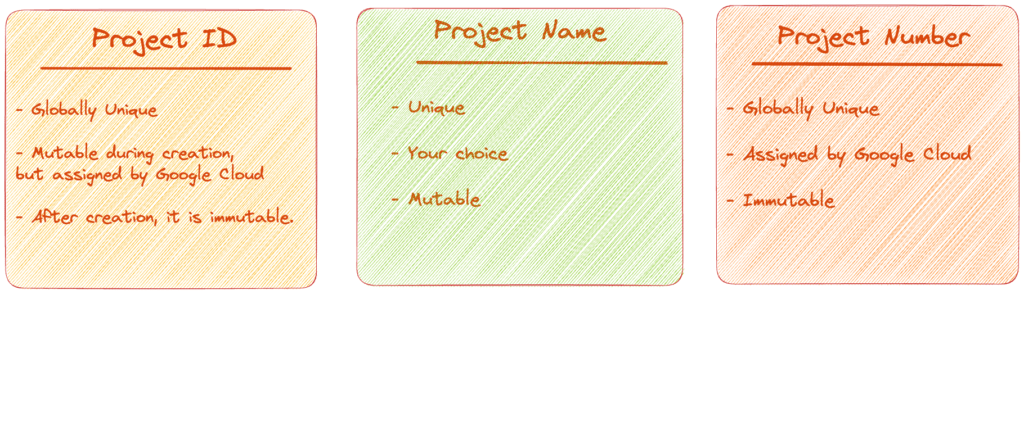
Each Google Cloud project has three key attributes: a project ID, a project name, and a project number. The project ID is a fixed, globally unique identifier assigned by Google. It is used to specify the project being worked on within Google Cloud. Conversely, project names are user-created, non-unique, and can be modified. Google Cloud also assigns each project a unique number, mainly used for internal resource tracking.
- Resources
Resources pertain to individual GCP services, including Compute Engine instances, Anthos , VPC Cloud Storage buckets, or BigQuery datasets. For ShopTrendy, resources might encompass virtual machines running their website, databases containing customer information, and data pipelines analyzing customer behavior.
Leveraging the hierarchical structure, ShopTrendy can efficiently manage its growing cloud assets, ensuring organized resources and robust, adaptable access control. We’ll explore Identity and Access Management (IAM) and the interaction methods available to GCP users in upcoming sections.
Next, we’ll address policy inheritance in GCP, a key aspect for effective access control and consistent policy application throughout the resource hierarchy. We’ll examine how policy inheritance works across organization, folder, and project levels, and how ShopTrendy can use it to maintain security, organization, and efficient resource management as the company grows.
Policy inheritance.
As we dive into the concept of policy inheritance in Google Cloud Platform (GCP) for newbies, let’s consider a real-world example involving ShopTrendy, an e-commerce company. Policy inheritance is a crucial aspect of managing access control and ensuring the consistent application of policies across the resource hierarchy.
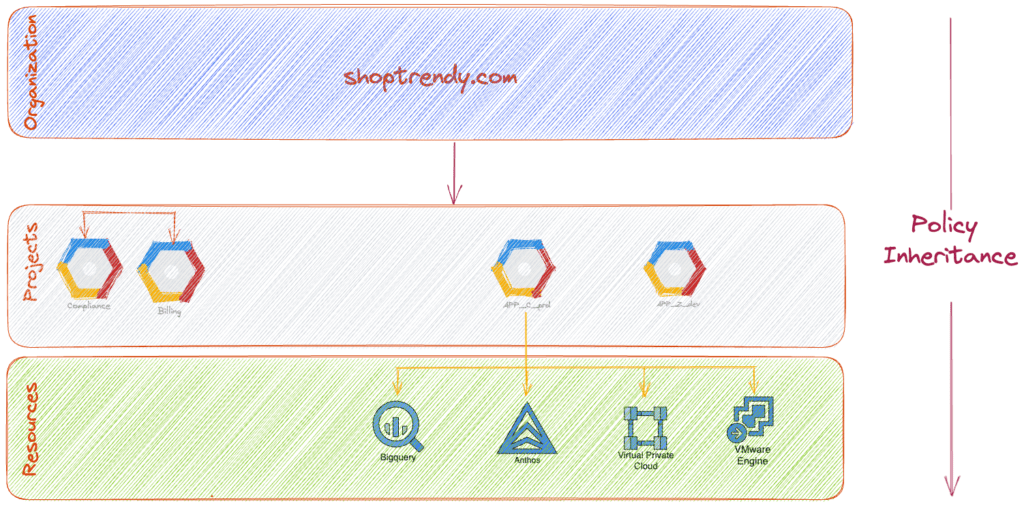
Let’s say that ShopTrendy wants to give a specific team access to view their sales analytics data. To do this, they can set an IAM policy at the folder level, which grants the team the ‘BigQuery Data Viewer’ role. This policy then gets applied to all projects within the folder, giving the team access to view BigQuery data across all those projects.
Now that we’ve seen how policy inheritance works in a real-world scenario, let’s explore some tips and best practices for leveraging it effectively in GCP. These tips are based on the ShopTrendy example:
- Be granular and use overriding: When applying policies, start with broad permissions at higher levels and then narrow down as you move to lower levels. Lower-level policies cannot override higher-level ones, so be careful when granting access.
- Follow the least privilege principle: Always grant users the minimum access they need to perform their tasks. This minimizes security risks. For instance, if a developer only needs to view logs in a specific project, grant them the ‘Logs Viewer’ role instead of a broader role.
- Use custom roles: Create custom IAM roles with specific permissions tailored to your organization’s needs. This way, you can grant only the required permissions, minimizing security risks and ensuring compliance with internal policies.
- Conduct regular audits and reviews: Periodically review and audit your IAM policies to ensure that they are up-to-date and aligned with your organization’s evolving requirements. Remove any redundant or outdated policies, and revoke access for users who no longer require certain permissions.
- Utilize organization policies: Leverage organization policies to enforce consistent rules across your GCP resources. For instance, you can create a policy to restrict the regions where resources can be deployed, ensuring compliance with data residency regulations.
By following these tips, ShopTrendy can effectively manage policy inheritance in GCP, ensuring a secure and well-organized environment that scales with the company’s growth. This way, they can maintain efficient access control and resource management.
Understanding Identity and Access Management (IAM)
In an organization with numerous folders, projects, and resources like ShopTrendy, it’s essential to manage and restrict access as needed. Administrators can use Identity and Access Management (IAM) to accomplish this.
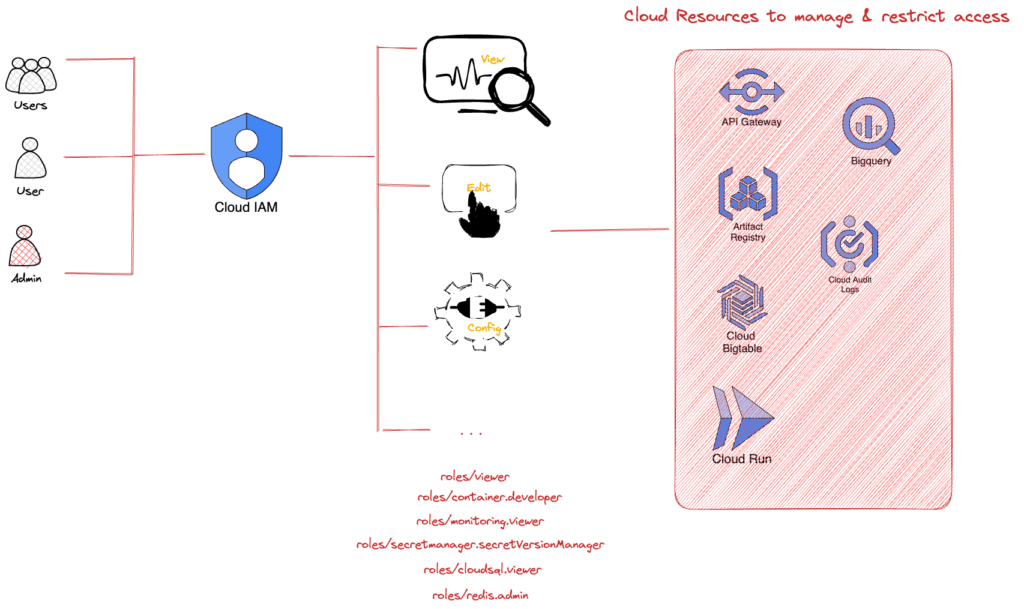
IAM is a critical tool for managing access and permissions to specific resources within your organization’s Google Cloud Platform (GCP). By using IAM policies, administrators can determine who can access which resources and what actions they can perform.
An IAM policy consists of two main parts: “who” and “what.” The “who” in a policy can be a Google account, a Google group, a service account, or a Cloud Identity domain. The “what” is determined by a role, which is a collection of permissions that define what actions can be taken on the resource. This makes it easier to manage and understand permissions, allowing for better control of access within the GCP environment.
Let’s take the example of ShopTrendy, an e-commerce company that uses IAM to manage access and permissions in their GCP environment. ShopTrendy has a project dedicated to inventory management and needs to grant access levels to their development and marketing teams to manage virtual machines (VMs) in the project.
To give the development team the necessary permissions to create, modify, and delete VMs in the project, ShopTrendy’s administrators assign the “Compute Instance Admin” role. The “who” in this case would be the Google group or Cloud Identity domain containing the development team members.
For the marketing team, who only needs read-only access to VM logs without the ability to modify or delete them, the administrators would assign the “Logs Viewer” role.
By using IAM policies, ShopTrendy’s administrators can effectively manage access control and permissions. They ensure that each team has the appropriate level of access to the resources they need while preventing unauthorized actions. This approach streamlines resource management, improves security, and ensures efficient collaboration among teams within the GCP environment. In the next post, we will delve deeper into IAM policies and explore more advanced use cases.
Delving into IAM Roles
IAM offers three types of roles: basic, predefined, and custom. Each role type caters to different organizational needs and access requirements within ShopTrendy’s Google Cloud projects.
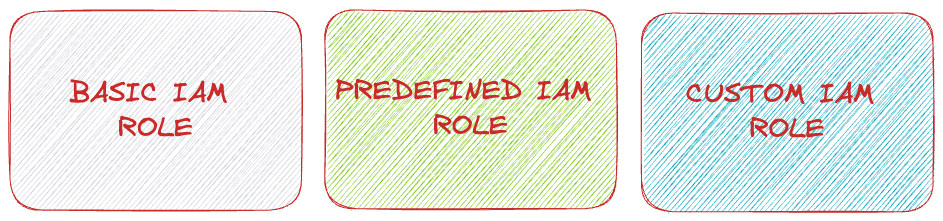
Basic roles
These roles are broad in scope, impacting all resources within a project. Basic roles include owner, editor, viewer, and billing administrator. However, basic roles might be too extensive for projects containing sensitive data.
- Project viewers: Can view resources but not modify them.
- Project editors: Can view and modify resources.
- Project owners: Can view, modify resources, manage roles, permissions, and billing.
- Billing administrators: Can manage billing without modifying resources.
Predefined roles
Google Cloud services offer predefined roles tailored for specific job roles. For example, Compute Engine provides predefined roles like “instanceAdmin” that can be applied to resources in a project, folder, or organization, allowing specific actions.
Custom roles
These roles adhere to a “least-privilege” model, granting individuals the minimum necessary access for their job. For instance, ShopTrendy might create an “instanceOperator” role, allowing users to start and stop Compute Engine virtual machines but not reconfigure them.
Let’s consider real world example ,to effectively manage access control and permissions within ShopTrendy’s Google Cloud projects, it’s crucial to understand and apply best practices for each IAM role type. Here’s a brief overview of when to use each role type and some real-world examples within the ShopTrendy context:
- Basic roles: Use these roles for general access control when fine-grained permissions are not required.
- Example: Grant the project viewer role to ShopTrendy’s QA team, allowing them to inspect resources without making changes.
- Predefined roles: Use these roles to grant more specific permissions tailored to particular Google Cloud services.
- Example: Assign the Compute Engine “instanceAdmin” role to ShopTrendy’s DevOps team, allowing them to manage virtual machines without granting access to other unrelated resources.
- Custom roles: Implement these roles when you need to adhere to a “least-privilege” model, granting the minimal necessary access for specific job roles.
- Example: Create a custom “instanceOperator” role for ShopTrendy’s junior DevOps engineers, permitting them to start and stop virtual machines without the ability to reconfigure them.
By understanding and implementing these best practices for IAM role types, ShopTrendy can maintain a secure and well-organized environment within their Google Cloud projects, ensuring that access control and resource management remain efficient and flexible.
Service Accounts Demystified
Imagine that ShopTrendy has an application running on a virtual machine in Google Cloud Platform (GCP) that needs to access data stored in Google Cloud Storage. To ensure secure access and prevent unauthorized access, they want to restrict data access only to that specific virtual machine, not everyone on the internet.
To achieve this, ShopTrendy can create a service account, which is a special type of Google account used by applications and virtual machines to authenticate with GCP services. The service account acts as an identity for the virtual machine, allowing it to access specific resources within GCP.
By granting the necessary permissions to the service account, ShopTrendy can ensure that only the virtual machine associated with the service account can access the data in Cloud Storage. This approach minimizes the risk of unauthorized access and protects sensitive data from potential security breaches.

In ShopTrendy’s Google Cloud projects, service accounts are an essential tool for managing secure access to resources. Service accounts are identified by an email address and use cryptographic keys instead of passwords to access resources.
Here’s an example Gcloud command to create a service account and grant it access to Cloud Storage:
gcloud iam service-accounts create vm-storage-access --display-name "VM Storage Access"
gcloud projects add-iam-policy-binding --member="serviceAccount:vm-storage-access@.iam.gserviceaccount.com" --role="roles/storage.objectViewer"
gcloud iam service-accounts keys create /path/to/key.json --iam-account=vm-storage-access@.iam.gserviceaccount.com
Note that <PROJECT_ID> should be replaced with the actual ID of the project, and the roles/storage.objectViewer role grants read access to objects in a bucket. You may need to adjust the role depending on the desired access level. Finally, the third command generates a JSON key file that can be used to authenticate the virtual machine with Cloud Storage.
Introduction to Cloud Identity
As ShopTrendy grows and adds new employees to its team, managing access to Google Cloud resources becomes increasingly important. While it may be tempting to use individual Gmail accounts and Google Groups to collaborate, this approach can quickly become unmanageable.
ShopTrendy can simplify access management for its workforce on GCP with Cloud Identity. Using the Google Admin console, admins can create policies and manage users and groups, while employees can use their existing Active Directory or LDAP systems to sign in.
If an employee leaves the company, disabling their account through the Google Admin console will revoke their access to all associated GCP resources immediately. This centralized and secure approach to access control ensures that only authorized personnel can access GCP resources, streamlining access management and maintaining data security.
Interaction Techniques for Google Cloud Platform (GCP)
As a new user of Google Cloud, it can seem overwhelming to understand how to access and interact with the platform. Fortunately, there are multiple ways to do so, catering to different user preferences and needs.
- Google Cloud Console:
The Google Cloud Console is a web-based user interface that allows users to access and manage Google Cloud resources using a web browser. This option is ideal for users who prefer a graphical user interface (GUI) and are not comfortable with command-line interfaces. With the Google Cloud Console, ShopTrendy can easily create and manage virtual machines, databases, and storage buckets.
- Cloud SDK and Cloud Shell:
The Cloud SDK and Cloud Shell provide a command-line interface (CLI) for accessing and managing Google Cloud resources. Cloud Shell is a web-based shell environment that allows users to run commands and scripts, making it a convenient option for managing resources on-the-go. With the CLI, ShopTrendy can automate resource management tasks and run scripts to set up and configure resources in bulk.
- APIs:
Google Cloud offers a range of APIs that allow developers to build custom applications and automate resource management. This method is suitable for users with programming experience who want to build custom solutions tailored to their specific needs. With APIs, ShopTrendy can automate tasks such as monitoring resource usage and creating virtual machines.
- Cloud Mobile App:
The Cloud Mobile App allows users to access and manage Google Cloud resources from their mobile devices. This method is ideal for users who are frequently on-the-go or need quick access to resources from their mobile devices. With the mobile app, ShopTrendy can monitor and manage their cloud resources from anywhere.
By providing multiple interaction methods, Google Cloud caters to a wide range of users with different preferences and needs. ShopTrendy can leverage these options to ensure efficient and effective management of their cloud resources. For example, an administrator can use the Google Cloud Console to manage resources while a developer can use the CLI to automate resource management tasks.
Conclusion
In this post, we’ve touched on some key aspects of Google Cloud, from its functional architecture to its identity and access management features. By understanding these features, you can make the most of Google Cloud and unlock new capabilities for your organization.
But this is just the beginning. There is so much more to explore in the world of Google Cloud, and in the upcoming segments of our post series, we’ll dive even deeper into these topics. So stay tuned for more insights, tips, and tricks to help you make the most of Google Cloud and take your organization to new heights.




